
Maximizing Security in Software Development: Expert Tips for 2023
Just how important is software security?
Well, according to the latest reports, it is estimated that cybercrime will cost companies around the globe 10.5 Trillion US by 2025. Yearly.
These numbers are truly staggering, but they also leave no doubt about why cybersecurity has become a priority for organizations.
So what to remember when developing software to make sure that the final product will be as safe as possible against any external threats?
In this article, we take a deep dive into software development security as a whole and cover some best practices for secure software development. Keep reading!
Contents
- What is software development security?
- What is a secure Software Development Policy?
- What is a secure software development lifecycle (SSDLC)?
- 6 phases of secure software development life cycle
- Why is security important in software development?
- Top 10 security practices for software development
- How can I secure my software development?
What is software development security?
Let’s start with the basics.
What exactly is software development security?
Is it designing an initial software architecture to be impervious to malicious attacks? Or Is it looking for potential vulnerabilities in a deployed system?
Well, this term is much more complex than that.
Software development security is the collective sum of all practices, processes, and technologies employed to ensure the security of software during the whole lifecycle of a development project – from conceptual work all the way to the final deployment.
It encompasses a wide range of measures, from threat modeling, vulnerability assessments, and penetration testing, to something as mundane as basic code reviews. All of these things have been set up with a sole purpose in mind – identifying and mitigating security risks in software.
By following secure Java software development practices, developers can create better and more secure software. Its benefits might not be immediately visible, but it will certainly save the company from very dangerous and costly data breaches and leaks in the future. By firmly integrating security into the software development process, organizations can greatly reduce the risk of security issues and ensure that their enterprise software is more resilient to attacks.
A well-defined software development policy should be the foundation for all software development security practices.

What is a secure Software Development Policy?
Since we’ve already mentioned it, we should also define secure software development policies. They constitute the backbone of all security-related practices and frameworks.
A secure Software Development Policy is a set of standards, guidelines, and procedures that define how software should be designed, developed, and maintained to ensure top-notch security throughout its entire lifecycle.

We can distinguish five key components of a good security software development policies:
- Good coding practices – This includes using secure coding techniques that all seasoned software developers should know, such as input validation and sanitization, to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS) attacks.
- Secure configuration management – This point involves procedures for managing software configuration and settings to prevent unauthorized access or changes to the software.
- Threat modeling – developers have to know how best to identify all potential threats and vulnerabilities to the software application and design appropriate countermeasures to mitigate those risks.
- Security testing – It involves various types of testing, such as penetration testing and vulnerability scanning, used to identify potential security weaknesses and vulnerabilities in the software architecture and design.
- Incident response and reporting – This point outlines procedures for responding to security incidents and reporting them to the appropriate authorities.
Alright, so we now know what goes into a secure software development policy, but how to create one?
Should you look into what the competition is doing in regard to software security? Or look up some checklists online?
Not at all!
In order to develop a comprehensive and effective security software development policy, organizations must first identify their security risks and requirements, as every company will have its own vulnerabilities. This can be done through an in-depth classic risk assessment, which should cover three main points:
- identifying potential threats and vulnerabilities,
- assessing the impact of these risks on the organization itself,
- determining the likelihood of these risks.
Based on the information gathered from this assessment, the company can then outline specific security measures and practices that need to be implemented to work best for their particular business scenario. Since no two custom development projects and applications are the same, each company and team of programmers have to have its own, distinctive security policy.
Over time, the advantages of a well-defined Secure Software Development Policy will become apparent in a multitude of ways. We are not even talking about greatly reducing the risk of security incidents within software applications, but about underscoring the role of security within each development project – a role that was often neglected in the past.
So to summarize, a secure software development policy ensures that software applications are developed with security features in mind, rather than adding them as an afterthought.

What is a secure software development lifecycle (SSDLC)?
Speaking of internal policies, we should also briefly touch on the development life cycle, as the two terms are quite closely related.
The secure software development life cycle (SSDLC) is a set of practices and processes designed to integrate security into every phase of software development projects.
Since SSDLC is a natural extension of the classic software development life cycle SDLC, its concepts should be present in various product-related activities from gathering business requirements and drawing initial designs, to the application deployment, and further maintenance.
By taking software security into consideration early on, organizations can identify and address potential vulnerabilities much faster, before they can be exploited by potential attackers. This results in software that is more resilient to attacks, reduces the risk of data breaches and enhances the overall security posture of the organization. Ultimately, a secure SDLC is essential for building and maintaining trustworthy software.
There are six typical phases of a secure software development life cycle:
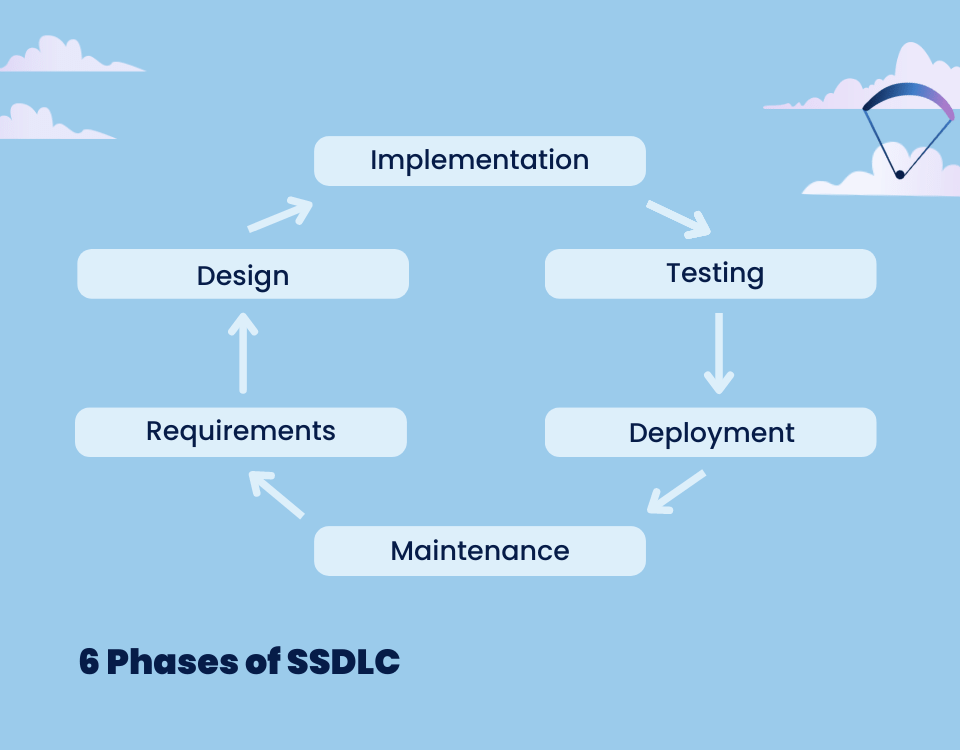
6 phases of secure software development life cycle
Requirements Analysis
In the first phase, keeping business goals in mind, the software development team works out all security requirements of the application, such as authentication, authorization, and encryption.
Design
The development team then creates a design that meets the security requirements identified in the first phase. This design should include security controls such as input validation, access control, and error handling.
Implementation
And now it’s time for writing the code itself with regard to all security issues revealed in the previous phase. In this part, code reviews should play a vital role in ensuring code quality and compliance.
Testing
In this phase, various testing methodologies are used to identify any security vulnerabilities in the application. It is important to mention that unit, security, and performance tests should be introduced right from the beginning and follow known good programming practices.
Deployment
Once the application has been sufficiently tested and all vulnerabilities have been found and addressed, it is ready to be deployed to the production environment.
Maintenance
Of course, there are no software architectures that you can just write and forget about. All software products require maintenance, and one of the most important parts of these post-deployment activities is security-related updates. This includes performing periodic security assessments, updating software components, and responding to any security incidents that may occur.
Read also: Power of Cloud Computing Scalability: Empowering Businesses to Scale with Ease

Why is security important in software development?
This question should be rather self-explanatory in today’s market.
But the statistic that we’ve mentioned in the beginning pretty much sums it all up. Security breaches are causing massive losses to companies across the world, and the problem is only getting worse as years go by.
Gartner predicts that by 2025, up to 45% of global organizations will be impacted in some way by software security breaches related to their supply chain. And dealing with vulnerabilities takes time. According to IBM, it takes an average of 277 days for security teams to identify and contain a data breach.
All of that means one thing: security is now more important than ever in software development, and taking appropriate measures will yield benefits to companies and users alike.
[Read also: Most common problems in software development]
Below, we’ve listed four key aspects in which software security is playing a pivotal role right now:
Protecting Confidential Information
According to Statista, last year in the US alone, there were a staggering 1802 cases of significant data compromises. These cases pertained to data breaches, leaks, and exposures, and collectively impacted over 422 million individuals. Despite the differences in the nature of these incidents, they all shared a commonality – they provided unauthorized threat actors with access to sensitive user data.
It is crucial to understand that these incidents do not discriminate and can affect anyone, from individuals to large corporations. Therefore, it is essential to take proactive measures to safeguard our data and prevent unauthorized access by threat actors.
Maintaining User Trust
A lot of users rely on software applications to safeguard their personal information and trust that their data is protected. But that hard-earned trust can be easily eroded if a software application is hacked or otherwise compromised, causing them to stop using the software or avoid future updates.
According to a survey conducted by the National Cyber Security Alliance, up to 80% of consumers said that they would stop doing business with a company if it experienced a data breach. Another survey by Accenture also found that 47% of online users cited security as the most important factor when choosing a digital service provider.
Preventing Business Losses
As we’ve already pointed out, security breaches can result in severe financial losses for the business or organization responsible for the software application. According to IBM, an average cost of a data breach in the US costs companies upwards of 9.44 million USD.
On top of that, companies may face legal and regulatory fines or lawsuits, as well as damage to their reputation, if it turns out that the data breach was caused by negligence on their part.
Compliance with Regulations
Many industries and governments have regulations and guidelines around data privacy and security that must be adhered to. Failure to comply with these regulations can result in fines and other penalties.
Through recent years, more and more governments and international bodies have expanded their data security policy. Both the EU and the US have developed extensive strategies focused on building collective capabilities to respond to major cyberattacks and working with external partners to ensure international security and stability in broad cyberspace.

Top 10 security practices for software development
Since we’ve finally got all the theory concerning software development out of the way, we can now focus on secure coding practices. These tips are intended to:
1. Treat software security as a priority right from the start
Before diving into coding itself, begin planning how you will integrate security into every phase of the SDLC – establishing thus the SSDLC that we’ve explained in great detail.
Programmers and product owners can, and frankly should, engage the power of automation in testing and monitoring vulnerabilities from day one. Security needs to be firmly baked into your team’s culture and code. There’s no better place to start than in the earliest phase of the software development process.
2. Educate employees and be proactive
This point may be less related to software development itself but it is really important in the long run nonetheless – especially to managers and people in charge.
Not only software developers but also regular employees, need to know what threats may be waiting for them online. They should be informed of common attacks and the basic practices on how to avoid them. To minimize the risks of negligence on the part of the employees, organizations often introduce zero trust policies for internal communications and data flow.
Developers on the other hand should have a deep security awareness in their work. The company should consider running regular training sessions that would include information about common software development vulnerabilities and ways of avoiding them. They should also keep track of the most common security issues from a trusted knowledge base.
3. Keep track of security practices with checklists
The software development process may be compared to a huge and complex machine. There are many moving parts that all have to come together to produce well-secured software that is aligned with business goals.
So, a great and easy way to help your team track security practices is using action checklists at regular intervals, such as weekly or monthly meetings. It will ensure that all necessary security policies and procedures are being actively implemented.
4. Employ a secure software development framework
A software framework is a pre-designed software architecture that provides a structured and organized approach to building software applications. It is basically the backbone of any modern software application. So which one is currently considered to be the safest? Let’s explore some of the most reliable options.
First and foremost, we have one of the most popular Java frameworks – Spring at our disposal. It offers developers a wide range of features to help prevent common security vulnerabilities, such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF) attacks. These features also include built-in support for secure password storage, encryption, and token-based authentication.
Another popular choice is Ruby on Rails. This framework is known for its strong security features, which have been refined over the years to provide maximum protection against common security threats.
Finally, let’s give a shoutout to Django, as it is yet another popular framework offering great security-related features. Like Ruby on Rails and Spring, Django incorporates a range of features to protect against the most common vulnerabilities like cross-site request forgery attacks and SQL injections.
[Read also: Top Software Development Methodologies: How to Choose the Right One?]
5. Use well-known and established libraries
As you all probably know, Java libraries are really powerful tools providing pre-built solutions for common programming tasks.
But programmers have to be extra careful while using their open-source counterparts.
There is a common assumption that open-source software is generally safer than proprietary software, as people think that if the code is developed and maintained by many people any security risks would be found and neutralized. In reality, though, this makes applications built using open-source libraries even more susceptible to vulnerabilities.
Why?
That’s because attackers can disguise themselves as contributors to the open-source library, and use it to gain backdoor access to the project. Therefore, Java developers should only use libraries from trusted sources and check them before integrating into the codebase.
6. Ensure complete data protection
Data protection is a very complex topic that deserves an article of its own but let’s briefly mention the important points to keep in mind.
First and foremost, developers should always use encryption when transmitting sensitive data. This means using secure communication protocols, such as HTTPS or TLS, to encrypt data in transit. Other than that, they should also use only strongly typed parameterized queries and variables to avoid unauthorized access, and never hard code connecting strings. The software application should also be set up to the lowest possible level of privilege when accessing the database itself.
When it comes to broader security strategy, the development team should also have the access to log data from daily cloud operations as it is crucial for any incident response plan. Without this knowledge, you may be left pretty much powerless when a security incident does occur.
7. Remember about authentication and password management
Year after year, the most commonly used password online is “password”.
Yeah, I know what you are thinking, that’s pretty stupid and irresponsible, but we as developers cannot do much about that apart from forcing users to use signs and capitalized letters in their passwords.
But what we can do is to ensure that in the backend of an application, passwords are handled with care and that the authentication methods are as secure as possible.
Programmers should use a centralized implementation for all authentication controls including libraries that call external authentication services. All authentication controls and password hashing should also be enforced only on a trusted system like the company’s server.
When it comes to the passwords themselves they should be encrypted and stored in a secure place and the source code is most certainly not a secure location.
8. Use code reviews to identify threats
Just as we’ve mentioned in our article on writing clean code, code reviews play a multitude of roles in programming projects and are not just for finding bugs and mistakes. One of such roles is looking for any potential security risks in your colleague’s code.
Your teammates should not hesitate to make remarks when they see an opportunity to use a better and safer approach to certain methods. And the same applies if you see a part of someone else’s code that may cause security issues – be sure to point that out during code review and propose a better solution if you have one in mind.
For every code change you make, you should go back and check to see if those changes have introduced any new security vulnerabilities. In addition, it is essential to review security requirements to ensure that secure coding practices are followed throughout the development process.
9. Use Static Code Analysis Tools
Speaking of code reviews, we should also touch on static code analysis tools as they are really important in finding software vulnerabilities. They can be integrated into the development pipeline so that every time there is a new build awaiting deployment, it will automatically run through these checks and flag any potential issues.
During a security code review, static code analysis tools may be used to identify areas of concern. These tools are essential for large organizations where developers may come and go or lack security knowledge. Static code analysis tools are not perfect, but they can certainly help catch some of the most common issues that lead to software vulnerabilities.
10. Protect code integrity
To sum up all of these good practices, we should also talk about code integrity, as it pretty well captures the essence of what makes software secure.
Code integrity is an essential aspect of software security that ensures that the code is being executed on a system that is authentic, unaltered, and free of any malicious modifications, thus safeguarding against unauthorized access and data theft.
To maintain good code integrity developers should first and foremost use version control to keep track of changes and ensure that all code modifications are properly documented. They should also keep everything in secure repositories allowing only authorized access to prevent tampering, as well as regulate contact with the code, monitor changes, and closely oversee new pushes to the main branch of the project.
When code integrity is maintained throughout the entire software development lifecycle, it results in a high-quality software product that meets the needs of users and stakeholders, but perhaps most importantly is free of any security-related risks.

How can I secure my software development?
As we’ve already mentioned in this article, securing the software development process requires a multi-faceted approach that encompasses various measures and practices – basically the fundamentals of the SSDLC concept.
Developers should, first, incorporate threat modeling, security-focused code reviews, and testing methodologies in their daily routines.
Secondly, developers should stay up-to-date with the latest security trends and technologies and update their software to address new threats. They should be on a constant lookout for important news regarding software security like the Log4J, or Google Chrome Zero Day.
Finally, it is good practice for software developers and product owners to run continuous security testing for software applications. Scanning tools will keep a close eye on all the possible fail points of web applications based on constantly updating security flaws databases. So no matter whether you are developing a SaaS application or an ecommerce website, you can use these security audits to improve software security and demonstrate to your clients that they can trust you with their data.
[Read also: How to Perform Successfull Website Security Audit: Checklist & Essential Tools]

Security software development practices – closing thoughts
These days, software security is absolutely essential because it protects against potential threats and attacks, such as data breaches and cyber-attacks.
A lack of security measures may result in compromised data, system downtime, and financial losses. Ultimately, investing in software security helps keep your applications secure and reliable, protecting both users and the organizations that develop and maintain them.
Related Posts
- How to Build an Inventory Management System: Key Steps and Tips
- How to Build a Document Management System: Alternative Approach
- Online Shopping Recommendations – Introducing Them to Your Business
- Amazon Product Recommendation System: How Does Amazon Algorithm Work?
- Movie Recommendation Systems: A Business Guide
Thank you for taking the time to read our blog post!