
Best Practices for Writing Secure Java Code
The Java platform remains popular with businesses and developers alike, and it’s hardly surprising.
It offers a high degree of modularity and portability, but perhaps most importantly, a wide range of security features to protect sensitive user data.
In this article, we will explore why Java is considered a secure language and how developers can use its security features to build reliable and secure applications. We will also discuss best practices for secure coding in Java and highlight some common security issues and vulnerabilities to watch out for.
Why software security is important?
Software security is essential in 2023, as cyberattacks continue to rise and become more sophisticated. According to Cybersecurity Ventures, cybercrime damage costs are projected to reach $10.5 trillion annually by 2025, up from $3 trillion in 2015. That represents a staggering yearly 35% increase.
Each individual data breach in the past years has caused significant losses to the companies affected. IBM estimates that 71% of breaches in 2021 were financially motivated, and the average cost of a data breach was $4.24 million.
There’s no doubt that cybercrime is a serious threat to organizations that are doing business online. But what about developers? Do they realize the seriousness of the risks posed by malicious attacks and data leaks?
Unfortunately no.
According to the results of the 2022 survey “The State of Developer-Driven Security” conducted by Secure Code Warrior, developers’ attitude towards cybersecurity is somewhat lackluster. The survey found that even though many developers recognize the significance of incorporating a security-led approach in the software development process, 86% of them do not consider application security as a primary concern when writing code.
These statistics underscore the importance of cybersecurity, both in terms of financial and reputational costs, as well as raising awareness among developers. Companies and organizations must prioritize software security to protect sensitive data, reduce the risk of cyberattacks, and perhaps most importantly, maintain customer trust.
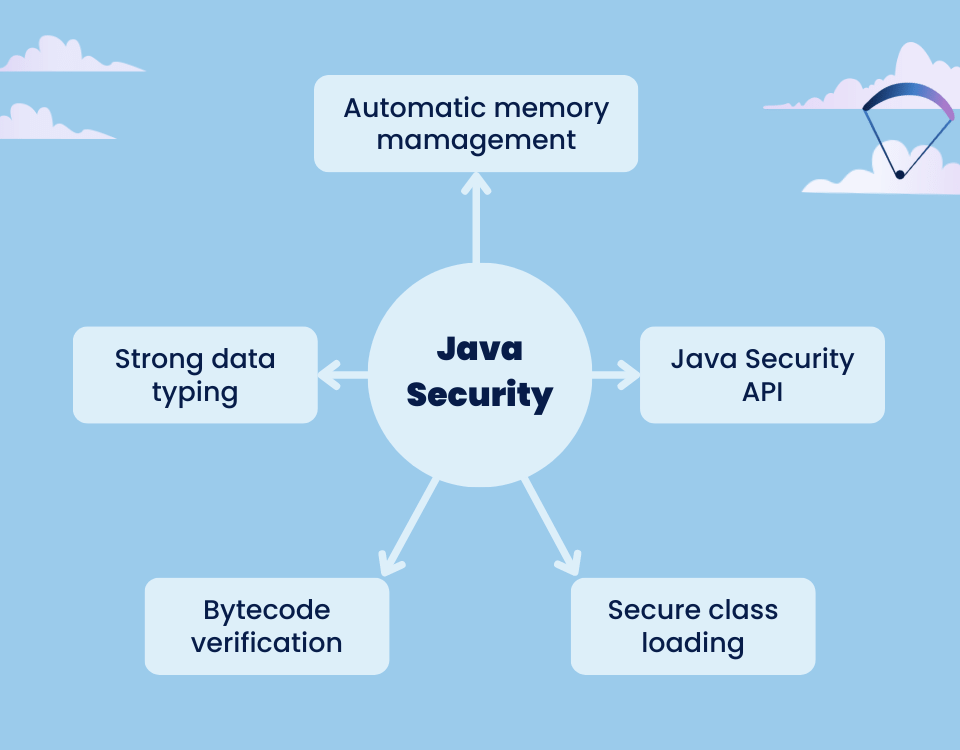
What Java features make it a secure programming language?
The Java language itself is inherently secure in many ways. A few of its features include:
Automatic memory management Java
One of the best features of Java is its memory management system, which uses garbage collection to automatically eliminate unnecessary objects. It ensures that the code is robust and clean. This feature is also beneficial security-wise because it greatly helps in software testing and thus reduces the likelihood of vulnerabilities. But perhaps even more important than that, it ensures that no traditional memory leaks may occur, as they are still considered to be a formidable threat.
Strong data typing
Because Java is a strongly typed language, it enforces strict code parameters on developers, which minimizes the occurrence of bugs and the potential security vulnerabilities that come with them.
Bytecode verification
During the compilation process, Java converts the code into bytecode that can run on any machine. It’s thus a platform-independent programming language. Java also provides built-in bytecode verification features that check the bytecode before execution, reducing the likelihood of malicious bytecode being included in the code.
Secure class loading
Dynamic class loading is another important feature of Java that allows software components to be installed at runtime. However, this mechanism of class loader also presents a potential vulnerability, as attackers could exploit it to load malicious files into the application.
Fortunately, the JDK team has implemented secure class loaders that evaluate each class file against the virtual machine’s access controller and apply context-specific policy standards. In addition, these class loaders enforce namespace-related rules that prevent malicious actors from forging classes and running them on the system.
Java security APIS
Java also provides a wide range of APIs designed for secure network communication with encryption, message integrity, and both client and server authentication. They allow developers to write secure Java code easier and faster compared to other languages.
- SSL/TLS: SSL and its successor, TLS, offer security for communication over untrusted networks by utilizing data encryption and public-key infrastructure. Java provides support of SSL/TLS through SSLSocket defined in the “java.security.ssl“ package.
- SASL: SASL (Simple Authentication and Security Layer) is a Java API that provides a framework for adding authentication and data security features to network protocols. SASL enables Java developers to incorporate multiple authentication mechanisms into their applications, such as username/password, Kerberos, and public key authentication. Java supports SASL as part of the “java.security.sasl“ package.
- GSS-API: Generic Security Service API (GSS) is a Java API that provides a framework for building secure client-server applications by allowing communication between applications to be secured with various security mechanisms such as Kerberos and SSL/TLS. It is designed to be independent of any specific security technology or authentication mechanism, providing a standard interface to various security services. Java supports GSS-API as part of the “java.security.jgss“ package.
Is Java secure by default?
Java is designed to be secure by default, with numerous built-in security features such as cryptography, authentication, and public key infrastructure available to developers.
In addition to these features, Java’s strong data typing makes its code security inherently more robust than some other programming languages. Moreover, thanks to a thriving developer community, the JDK receives regular updates that continually improve its security capabilities.
But let’s be clear about one thing: no programming language is completely secure by default.
Java security ultimately depends on how well the code base is written and configured. Therefore, it is imperative that developers follow secure coding practices, use only trusted libraries, sanitize all inputs, and implement access control mechanisms to ensure the security of Java applications.

Java framework security features
Java frameworks are essential tools for developers as they provide them, with a set of tools, components, and pre-written code libraries to build applications faster and more efficiently. Frameworks are also relevant from a security perspective, as they create an additional layer of functionality aimed at minimizing potential vulnerabilities.
Among the many options on the market, one of the most popular Java frameworks is Spring. The Spring Security Framework provides some additional security features that make it easier for Java developers to create secure Spring-based applications. Some of these features include additional authentication, authorization, encryption, and access control.
We should also briefly mention Spring Security.
It is a widely used module of the Spring Framework that provides a comprehensive security solution for Java applications. It includes support for both basic and advanced authentication and authorization mechanisms supported in both Servlet and WebFlux environments, as well as features such as password-based authentication hashing, CSRF protection, session management, and much more. Spring Boot also provides automatic configuration for Spring Security, making it easy for developers to integrate these security features into their applications.
[Read also: Top Software Development Methodologies: How to Choose the Right One?]
7 Best Practices for Writing Secure Java Code
Writing secure Java code is, without a doubt, not an easy feat. Just like in the case of improving your craft as a software developer, there are some best practices to follow.

1. Write clean, strong Java code
Let’s start with one of the most universal coding tips – writing high-quality, clean code.
Writing clean code in Java is important from a security standpoint because it helps improve the maintainability and readability of the code. Clean code makes it easier for other developers to understand the codebase and make changes without introducing new bugs.
It also makes it much easier for your teammates to spot potential vulnerabilities and alert you to them during code reviews.
In addition, writing clean code can reduce technical debt and improve the overall code quality, of the software, making it more reliable and secure.
2. Only Use Tried and Tested Libraries
Now let’s move on to libraries, as they are often one of the main sources of security problems.
Using untested or unknown libraries can be risky because they may contain vulnerabilities that attackers can exploit. In addition, these libraries may not receive regular updates and maintenance, leaving the application vulnerable to newly discovered exploits.
Using proven libraries that are regularly maintained and updated is therefore one of the most important rules for improving software security. Use only these libraries that have been widely used and tested by the development community, since any vulnerabilities in them are likely to have been identified and addressed long ago.
In addition, developers should regularly update their libraries to ensure that their application remains secure.
[Read also: The most common problems in software development]
3. Writing secure Java code also consists of a myriad of various small tips and coding practices aimed at improving Java security.
Using these secure coding practices is important because every little bit helps in defending against security breaches, data leaks, system compromises, and other types of cyberattacks.
Secure coding practices in Java include using proper error and exception handling, using secure input validation, avoiding the use of insecure coding constructs such as race conditions and buffer overflows, and using strong and reliable access control and authentication mechanisms.
By following secure coding practices, Java developers can reduce the likelihood of introducing security flaws into their applications and improve the overall security posture of their systems.
4. Use strong cryptography
Cryptography is the practice of securing information by converting it into an unreadable format that can only be deciphered by authorized individuals. Using strong cryptography in Java is one of the most important security-related practices because it helps ensure the confidentiality, integrity, and authenticity of sensitive data.
Strong cryptography provides a high level of security against various types of attacks, such as eavesdropping, tampering, and data theft. By using strong cryptographic algorithms such as AES in Java applications, developers can protect sensitive data such as passwords, credit card numbers, and personal information from unauthorized access.
To further assist developers, Java provides a robust set of cryptographic APIs that developers can use to implement strong encryption and decryption capabilities in their applications.
To leverage strong cryptography in Java, developers can utilize the Java Cryptography Architecture (JCA) framework. It provides access to cryptographic functionalities in Java, including:
- Digital signatures
- Message digests
- Message authentication codes
- Symmetric and asymmetric ciphers
- Key generators and key factories
However, it is still important to ensure that the Java environment is correctly configured to support strong cryptography and to follow best practices for key management and secure storage of sensitive data.

5. Sanitize all input
In many data breaches, hackers gain access to sensitive information by inserting malicious data into the system. For example, an attacker could enter malicious code into a form field, such as a login form, which could then be executed by the application, giving the attacker access to sensitive information or control over the system.
For this reason, sanitizing all input in Java programs is a key aspect of maintaining a proper level of security in Java code, as it helps to prevent security vulnerabilities that can arise from user input. The most prominent of these attacks are cross-site scripting (XSS) attacks and SQL injections.
Cross-site scripting (XSS) attacks involve injecting malicious code into a web page viewed by other users. Once injected, the code can execute in the context of other users’ browsers, potentially allowing attackers to steal sensitive information or perform unauthorized actions on web sites on behalf of the user.
SQL injection attacks, on the other hand, involve injecting malicious SQL code into a Website’s database query. This can be done through user input, such as a search bar or login form, if the Website does not properly validate or sanitize the input. Once injected, the code can execute unauthorized database queries, potentially allowing attackers to view, modify, or delete sensitive data.
These examples underscore the importance of input sanitation. This process usually involves validating, filtering, and encrypting all user input to ensure that it is safe for use in an application. Failure to sanitize input is a serious security risk because it can leave an application vulnerable to attacks that compromise the confidentiality, integrity, and availability of sensitive data.
[Read also: What Is a POC and How to Create a Proof of Concept?]
6. Protect access control
Just as authorized access can be gained by inserting malicious files into the system, it can also be gained through simple negligence. That’s why access control is another area of focus in cybersecurity.
Java developers can achieve access control in Java using the Policy and Permission classes, mediated by the SecurityManager class. The SecurityManager is part of the java.lang package and is responsible for enforcing access control checks in Java. Programmers should also implement authorization checks to ensure that users are authorized to access the resources they are requesting. This may involve checking the permissions assigned to a user’s role, checking user attributes, or checking other access control policies.
When it comes to developing internal systems, Java programmers should also implement role-based access control (RBAC) to ensure that users have access only to the resources they need to perform their tasks. This involves defining roles, assigning permissions to those roles, and assigning users to the appropriate roles.
Finally, developers should regularly review and update access control policies to ensure that they reflect current business needs and security best practices.
7. Rule Scan and update your dependencies for known vulnerabilities
Just as Java developers beef up their defenses, hackers are constantly looking for new software vulnerabilities to exploit.
For this reason, all programmers should keep an eye out for newly discovered security risks and constantly improve their security.
Java developers should update their dependencies for known vulnerabilities using dependency management tools such as Apache Maven or Gradle, which can automatically detect and report out-of-date dependencies.
They can also use tools like Scanrepeat to scan their projects for known vulnerabilities and update the affected dependencies to their latest secure versions. They enable automated security testing of your web application with no code changes. On top of that, developers should also regularly monitor the vulnerability databases and mailing lists for the libraries they use and update their dependencies accordingly.
Sometimes Java vulnerabilities are so severe that they even make mainstream news, as in the case of Log4Shell (CVE-2021-44228), which was disclosed in December 2021 and affects applications running vulnerable versions of Apache’s Log4j. In such cases, you need to act quickly and efficiently to protect sensitive resources.
Java popularity statistics
It may be lacking in some aspects, but even in 2024, Java is still an incredibly popular programming language.
Java’s global developer usage stands at 30.55%, continuing its over thirty-year reign as a widely used and adopted programming language.
According to the PYPL Index, it’s the second most favored language. Oracle reports that 69% of developers utilize Java, and there are 51 billion JVMs operational. Despite its market share decreasing from 31% in 2008 to 15.81% in 2024, Java’s superior performance, ease of use, and scalability secure its critical role in worldwide enterprise solutions.
You might not see Java being used is some new startups, but most of the world’s fintech software architecture and enterprise systems are built upon this solid and prevalent programming language solidifying its role and position in the future.
Conclusion
If you want to develop an application that deals with user passwords and other sensitive information, you need to choose a tech stack that is equipped with top-notch security features.
Fortunately, the Java programming language and its supporting frameworks and technologies provide solutions and tools that can help developers write software that complies with the latest secure programming practices.
Related Posts
- 23 Best Books for Software Engineers in 2023
- Java Best Practices That Every Java Developer Should Know in 2024
- Best AI for Coding: Top 10 AI Tools for Software Developers in 2025
- Is Java Dead in 2024? The Truth About Java Popularity
- Introduction to Mojo Programming Language: New Era of AI Programming
We are Stratoflow, a custom software development company. We firmly believe that software craftsmanship, collaboration and effective communication is key in delivering complex software projects. This allows us to build advanced high-performance Java applications capable of processing vast amounts of data in a short time. We also provide our clients with an option to outsource and hire Java developers to extend their teams with experienced professionals. As a result, our Java software development services contribute to our clients’ business growth. We specialize in travel software, ecommerce software, and fintech software development.
