
Strangler Pattern for Application Modernization
At a time when technology is evolving at breakneck speed, the Strangler Pattern offers a lifeline to organizations struggling with outdated software systems.
This article delves into the intricacies of this unique approach to legacy modernization that incrementally transforms old applications into modern, efficient enterprise software.
We explore its practical applications in areas ranging from object-oriented programming to enterprise database upgrades, and highlight its ability to minimize risk while ensuring continuous operation.
Maintaining legacy monolithic application
One of the things software developers hate the most is working with the legacy codebase.
And there’s a reason for that.
These outdated systems often lack the flexibility and scalability of modern software designs, making it difficult to integrate new features or adapt to changing business needs. The code base in legacy systems is typically complex and poorly documented, which slows development and increases the risk of introducing new bugs during updates.
But the thing is, no matter how old they are, these systems still provide core functionality to the businesses that run them. In other words, they are still essential.
So these companies need to be smart about modernizing these outdated legacy software systems in the most convenient way possible. From an enterprise perspective, modernizing existing legacy software architecture is critical to maintaining a competitive edge. Modern systems are more efficient, scalable, and secure, offering better performance, user experience, and increased business value. They also offer greater flexibility to adapt to market changes, integrate with new technologies, and meet evolving customer demands.
According to Gartner well-established formula there are four approaches to application modernization:
- Rehost,
- Refactor,
- Relocate,
- Replatform
In this article, we will focus on the last one – replatforming but done in such a way that the entire application is moved to a brand-new environment without disturbing the day-to-day operation of the entire system.
Sounds interesting?
So let’s go down to the business and talk about strangler architecture pattern.
Understanding the strangler pattern
Imagine you have an old car that’s been reliable for years, but it’s starting to show its age. Instead of buying a brand new car, you decide to upgrade it piece by piece.
You might start with something small, like replacing the car’s worn out tires, and then move on to the more critical elements, like the clutch, brakes, and transmission. You might even throw in a few quality-of-life improvements like a modern infotainment system and better car audio.
Eventually, after a while, you realize that your old car has been transformed into something much better. It’s still the same car, but now it’s more reliable, safer, and more enjoyable to drive. And because the improvements were made incrementally, you could still use it for everyday tasks during the entire process.
That’s basically how the strangler architecture pattern works, but instead of a used car, we’re modernizing legacy software.
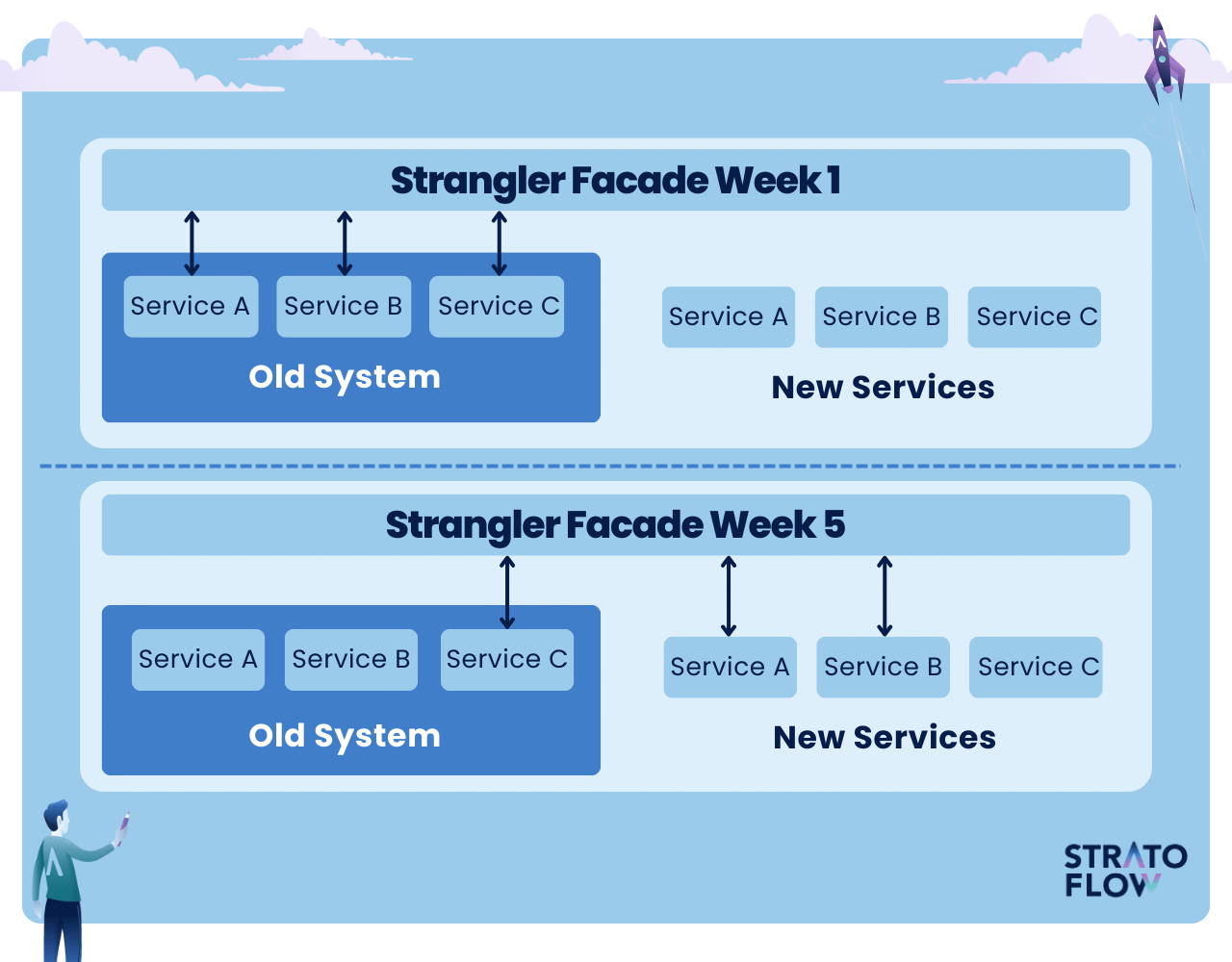
The Strangler Pattern is a technical strategy for modernizing legacy applications in a controlled and incremental manner. In this approach, new functionality is gradually built and encapsulated around the existing legacy system. Over time, these new components ‘strangle’ the old system and original code, taking over more and more of its responsibilities.
Initially, a facade is created by development teams to intercept calls to the legacy system. This facade then redirects these calls to the new components or passes them through to the old system, depending on which parts have been modernized. As the modernization progresses, less traffic goes to the old system, and more is handled by the new, modern components.
The reason it’s called the “Strangler Pattern” is that it resembles the way a strangler fig grows: it slowly wraps around and eventually replaces the host tree. Similarly, in software, the new system slowly and steadily replaces the old one, ensuring a smooth transition with minimal risk of disruption to the business.
Key Pros of the Strangler Pattern
Exploring the key benefits of the Strangler Pattern reveals how this approach strategically overhauls legacy systems and brings significant benefits to businesses in the digital age. Let’s take a quick look at those benefits:
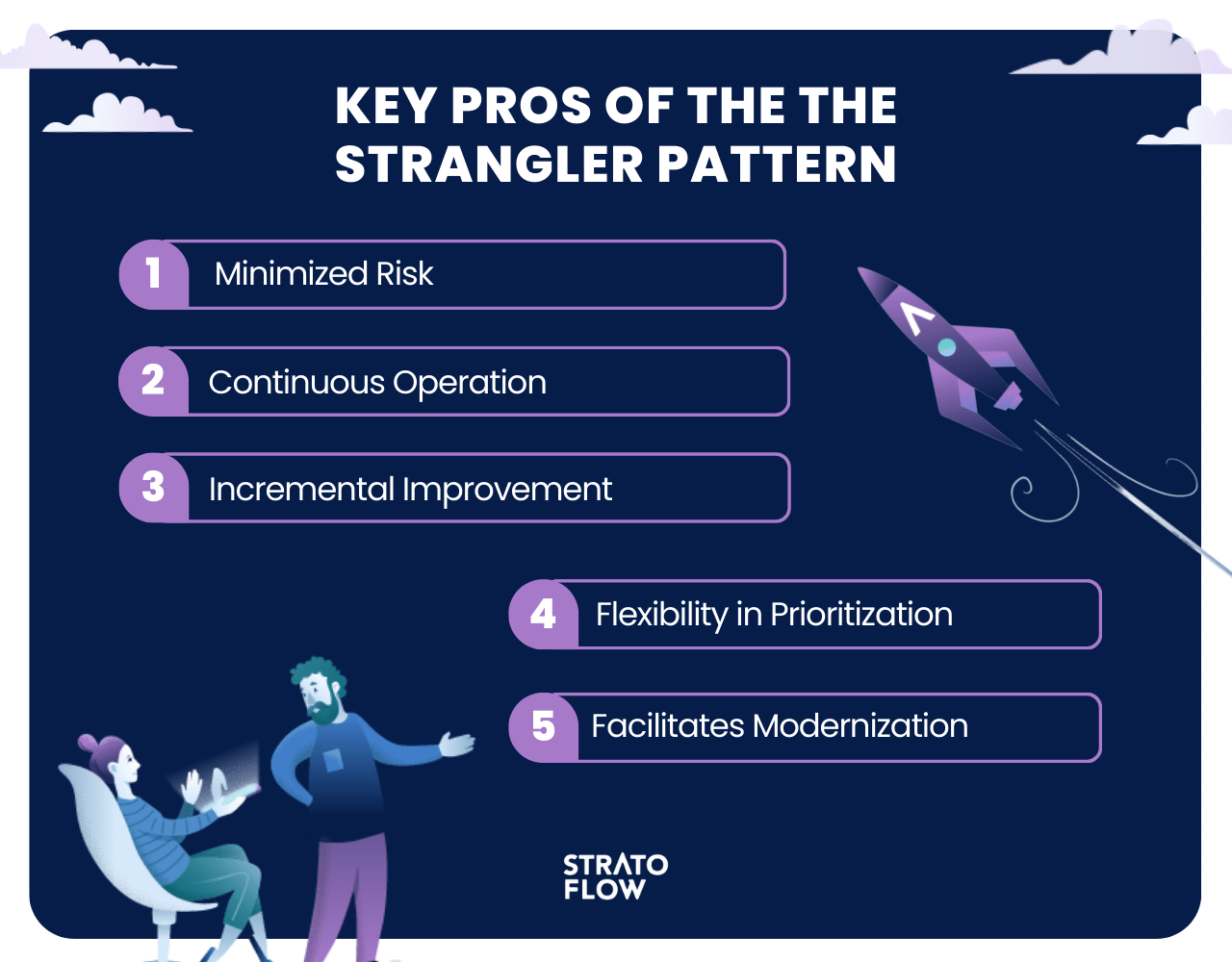
Minimized Risk
The Strangler Pattern significantly reduces the risk associated with system upgrades.
In a traditional overhaul, replacing an entire legacy system at once can cause major disruption if something goes wrong. But by replacing components incrementally, the Strangler Pattern allows organizations to test and validate each piece as it’s integrated.
This incremental approach ensures that any problems can be identified and resolved early, preventing large-scale outages and maintaining system stability throughout the transition.
Continuous Operation
Perhaps the most important benefit that comes to mind when thinking about the strangler pattern is the continuous operation of business services.
Unlike a complete system shutdown for upgrades, this method allows the old system to run concurrently with the new components. This dual operation ensures that business functions are not disrupted, maintaining service availability for customers and internal users.
As a result, businesses can continue to operate without the downtime or service interruptions typically associated with system overhauls.
Incremental Improvement
Another essential benefit of this approach is that it allows for incremental improvement of the system.
Each component replacement or update can introduce new features, enhanced performance, or better security. This gradual improvement aligns well with agile development practices and enables businesses to adapt quickly to market changes or new requirements. It contrasts with the traditional ‘big bang’ updates, where improvements are only realized at the end of a long software development cycle.
Flexibility in Prioritization
With the Strangler Pattern, organizations have the flexibility to prioritize which parts of the system to upgrade first based on their needs and resources.
This prioritization is critical to managing resources effectively, especially in complex systems where some components may be more critical or outdated than others. By focusing on high-priority areas first, organizations can address their most pressing needs sooner, resulting in early benefits and better allocation of development effort.
Facilitates Modernization
Finally, the Strangler pattern facilitates the modernization of legacy systems by enabling the seamless integration of new technologies and architectures.
As legacy application components are replaced, newer technologies can be introduced that may not have been compatible with the old system as a whole. This selective application migration process makes it easier to keep up with technological advances and ensures that the system evolves in line with modern standards and practices. This evolutionary process keeps the system relevant and efficient for the long term.
[Read also: How to Hire Dedicated Developers – Your Ultimate Guide]
How to implement the strangler pattern
The Strangler pattern uses a strategic, phased approach that relies heavily on a facade interface to modernize legacy applications. First, a facade interface is created. This facade acts as an intermediary layer, intercepting calls to the legacy system. It plays a critical role in deciding whether a request should be processed by the legacy code or redirected to the new components.
As the modernization progresses, more and more functionality is moved from the old system to the new. For each piece of functionality that is replaced, the facade routes requests to the new implementation instead of the legacy system. This gradual transfer of responsibility ensures a controlled and measured upgrade process.
During this phase, both the legacy and new systems operate in parallel. The facade manages the interaction between these critical systems, providing a seamless experience for end users. They are unaware of the underlying changes because the facade maintains a consistent outward behavior.
Over time, the new system grows in capability, slowly “strangling” the old system as it takes over more of its responsibilities.
Case 1: Object-oriented programming
In the context of object-oriented programming (OOP) like Java, the strangler pattern can be used to refactor and modernize applications that rely on outdated or inefficient object-based data structures and architectures.
A common scenario is dealing with a “god class“-a single class in a system that has become too large and unwieldy, taking on too many responsibilities. In applying the strangler pattern to OOP, the first step is to create a facade around this god class.
This facade acts as an intermediary, intercepting calls and redirecting them either to the original class or to new, more modular classes. The role of the facade is critical in managing the transition from the old, monolithic structure to a more distributed and maintainable architecture.
The process then involves the incremental creation of new, smaller classes that take over specific responsibilities from the god class. These new classes are designed to be more focused, adhering to OOP principles such as encapsulation and single responsibility. As these new classes are developed and tested, the facade gradually redirects more calls from the god class to these new, specialized classes.
Eventually, the responsibilities of the original god class are completely offloaded to the new, more efficient classes. The overall system design becomes cleaner, with well-defined, maintainable, and scalable object-based data structures. This modernized architecture improves the system’s performance and maintainability, and aligns it with current OOP best practices.
[Readl also: Complete Guide to Software Development Outsourcing for 2024]
Case 2: Web applications
In the modernization of web applications, the Strangler Pattern is particularly effective, especially when transitioning from traditional server-based Java applications with hard-coded SQL statements to dynamic, web-based services. This transition often involves moving from a monolithic architecture to a more flexible, service-oriented model.
The process begins with the identification of the components within the legacy Java application that are prime candidates for modernization. The goal is to replace these with more dynamic, maintainable, and scalable solutions.
A facade is introduced to reroute requests between the old and new parts of the application.
The new services are typically built using modern web technologies, offering greater flexibility and efficiency compared to the traditional, server-based Java application. They are designed to be loosely coupled and independently deployable, which enhances the overall scalability and maintainability of the application.
Eventually, the old system is completely strangled, and the application fully transitions to the modern, service-oriented architecture.
[Read also: What You Need to Know About Custom Development in 2023]
Case 3: Databases
In the context of enterprise-class databases that operate primarily through trigger-based mechanisms, the Strangler Pattern provides an effective framework for modernization. This approach is particularly relevant when dealing with large, complex databases that require both high reliability and minimal downtime during the upgrade process.
Given the trigger-based nature of these systems, triggers are used to replicate data changes from the legacy database to the new database in real-time. This setup ensures continuous synchronization and allows both databases to operate in parallel during the transition.
As the migration progresses, more and more data and functionality is transferred to the new database. At the same time, applications that previously interacted with the old database are gradually redirected to the new system. This redirection is carefully managed to maintain operational consistency and avoid disruptions to business processes.
Once the new database has fully assumed the role of the old system, with all the necessary data and functionality integrated, the legacy database can be decommissioned.
[Read also: Software Development Process: Comprehensive Guide]
Modernizing legacy systems with Stratoflow
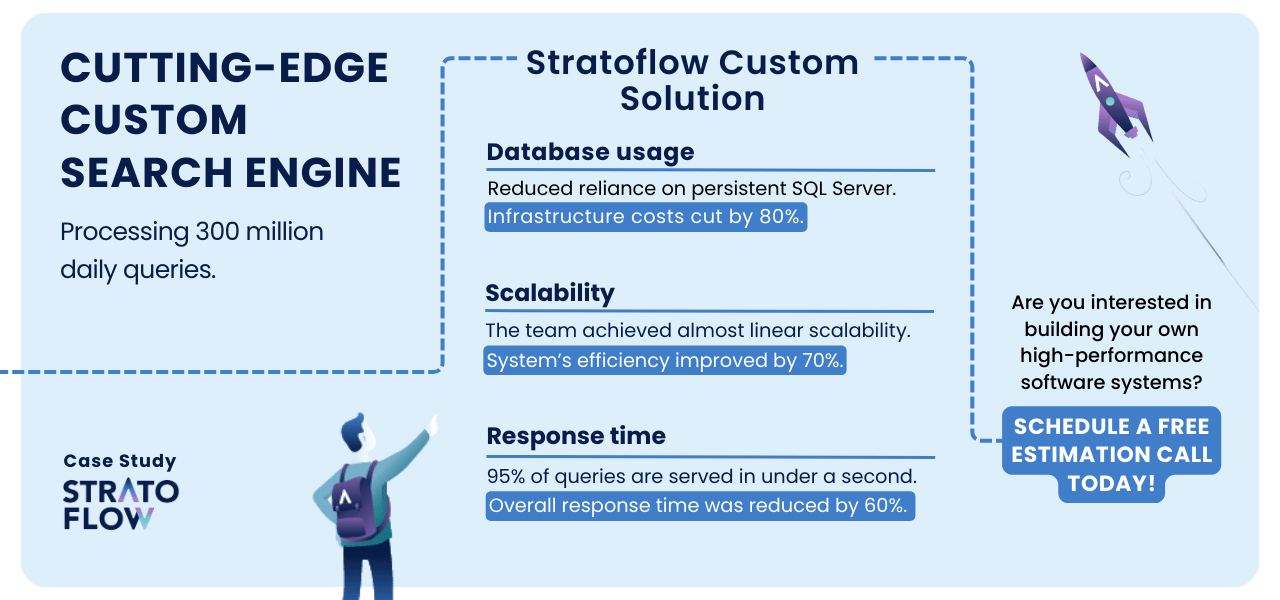
Stratoflow has demonstrated remarkable expertise in modernizing legacy software systems, as exemplified by the case study of a travel search engine.
Our developers successfully redesigned a system that was originally based on a cluster of SQL Server machines that had reached its scalability limits.
By introducing an in-memory data grid (IMDG) platform and a custom data loading mechanism, Stratoflow achieved significant performance improvements. This modernization resulted in an 80% reduction in infrastructure costs, 70% efficiency in horizontal scalability, and a 60% reduction in response times.
If you’re looking to improve your business through software modernization, let Stratoflow guide you on this transformative journey.
Our team is ready to work with you to customize solutions that meet your unique business needs and goals. Contact us to explore how we can help you achieve remarkable results and stay ahead in the digital age.
Conclusion
In conclusion, the Strangler Pattern emerges as a pivotal strategy in the field of application modernization, offering a structured yet flexible pathway for businesses to evolve their legacy systems.
Its ability to facilitate gradual, risk-mitigated transitions not only enhances operational efficiency but also positions enterprises to harness the full potential of modern technological advancements.
Related Posts
- How to Build an Inventory Management System: Key Steps and Tips
- How to Build a Document Management System: Alternative Approach
- Online Shopping Recommendations – Introducing Them to Your Business
- Amazon Product Recommendation System: How Does Amazon Algorithm Work?
- Movie Recommendation Systems: A Business Guide
Thank you for taking the time to read our blog post!

